They regularly need to see a wide range of websites to collect data. An auditor ought to be appropriately educated concerning the organization and also its vital small company tasks before carrying out a data center review. As an example, your cybersecurity auditors could inspect a box that claims you have actually obtained a firewall in position to cut down the series of sites employees can visit when utilizing company tools. If you're an auditor, that generally implies you will certainly require to function even more tough to differentiate yourself in the market. At the close of the program, you are going to be the most preferred auditor by the various device of organisation.
Before you conduct your really initial audit, make sure you document all your cybersecurity policies and http://www.bbc.co.uk/search?q=data protection policy also procedures. Mindful evaluation needs to be done to comprehend the resilience of service. A protection assessment aims to provide the exact same assessment as well as mitigation of threats for your whole company framework. Therefore, the range of an analysis methodology has a http://edition.cnn.com/search/?text=data protection policy lasting result.
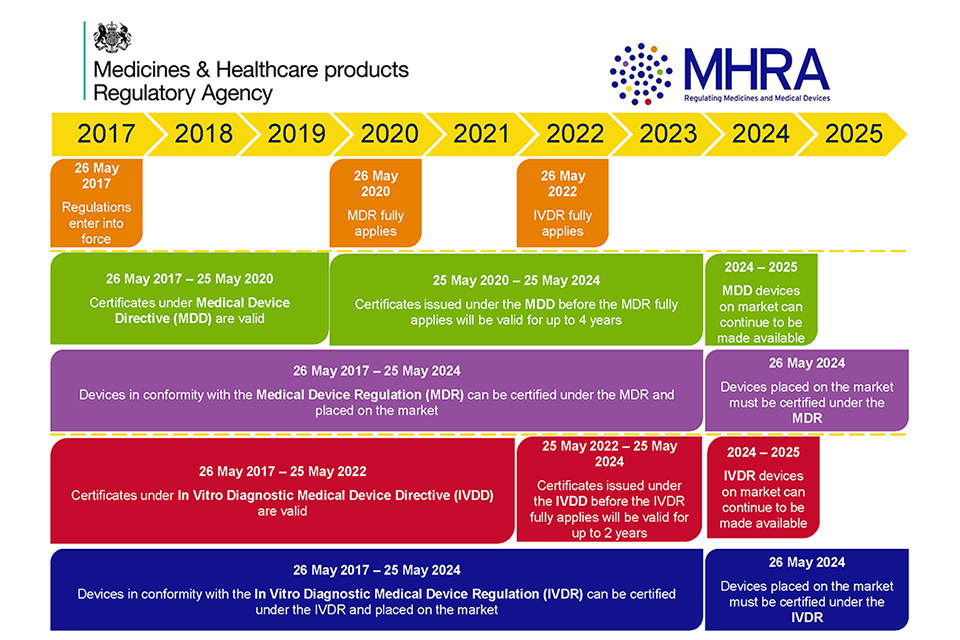
The previous portion of defining the reach of the evaluation would certainly be the innovation element. It can include company units, areas, systems as well as also third parties. The really primary step is to define the scope, for example, number and also kind of centers to be examined.
Even more info worrying the activities and strategies of the ISA99 committee gets on the ISA99 committee Wiki site. Remote accessibility should be logged.

There's an ability to check out online sessions and obstruct user accessibility if essential, permitting you to properly protect against any type of violations. The ability to open Microsoft Excel documents is important. The certain use of resources is set by means of the application individuals using application protection.

In some instances, a control may not be connected to your small business. Such systems may be called systems-of-systems. Organizations operating in controlled sectors might be asked to use an independent 3rd party to implement the analysis.
The sensible safety and security devices made use of for remote accessibility should be fairly stringent. Protected translation software is a vital component of your organization's danger management strategy.
If you're not familiarized with the services that you need, think about providing an RFI, instead of an RFP. Sometimes business execute void evaluation before the start of ISO 27001 application, so as to discover a feeling of where they're right now, privacy policies gdpr as well as to identify which sources they will wish to utilize as a method to carry out ISO 27001. Every single day, one more business becomes hacked and also makes the news. Your company could just be starting on the marketplace.
Danger management is rather essential. If monitoring establishes that the institutions maturity levels aren't suitable in link to the intrinsic risk profile, management needs to consider decreasing integral threat or developing a method to enhance the maturation degrees. The stakeholder administration obtains essential.